Axians Professional Service Team blogging from the Lab and providing the latest tech news.
Pulling Configs from Cisco NSO using curl and json2yaml.py
Mar 18, 2019 10:25:05 AM / by Axians UK posted in Guest blog, curl, Cisco, Axians UK News, Open Source, Infrastructure, Next Generation Networking, NSO, Network Automation, Innovation
Larger DDoS attacks adding power to potency
May 11, 2017 3:15:40 PM / by Axians UK posted in Verisign, Technology News, ddos mitigation, DDoS attack, security, DDoS, Technology, infosecurity, cyber attac, Malware, Infrastructure, Axians, cyber security, cyber crime, Security Assessment, Infosec, Network Managers
Malware and processing muscle to rent is swelling hacker armouries
Distributed denial of service (DDoS) attacks have severe consequences for their victims, causing considerable operational disruption and undermining trust in the organisation amongst customers, end users and business partners.
Software Defined Secure Networks: An Interview with Ken O’Kelly, Consulting Engineer, Juniper Networks
Dec 5, 2016 1:31:14 PM / by Axians UK posted in Secure Networks, Firewalls, security, Software Defined, SDN Overlay, Overlay, Technology, Higher Education technology, Junos Space, vmWare, Malware, Infrastructure, Education Tech, SDSN, Axians, Software Defined Secure Networks, Axians Vendor News, Juniper Networks, computer
Ken O’Kelly has been a key consultant in Juniper Networks; UK and Ireland security business for the past four and a half years. He previously held various roles (latterly as a security architect) during a 14 year stint with Imtech ICT.
Ken tells Axians about Juniper’s latest software defined security network (SDSN) solution and how it will make life easier for IT departments tasked with controlling network access for thousands of users.
Q: What is Juniper’s software defined security network (SDSN)?
SDSN is all about changing how you build the network. Traditionally organisations have tended to build security into the perimeter and everything outside that perimeter is untrusted and everything inside it is trusted. That is a bit of a challenge these days given that we all take our laptops and smartphones outside of that trusted barrier when we go home, where malware can infect them and vulnerabilities can be compromised. We then bring the device back inside the network perimeter and now it is trusted again and that gives any threat carte blanche to get around the network.
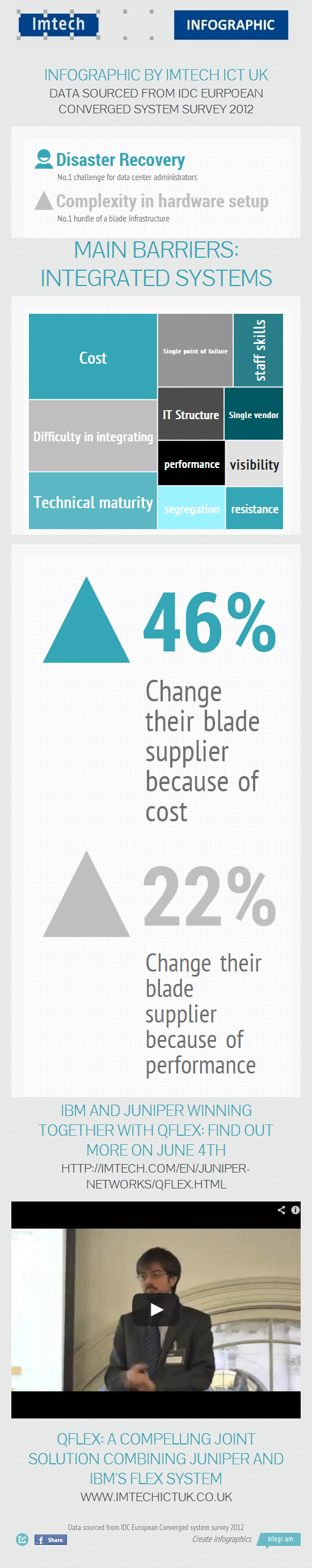
Challenges for a Converged Systems
May 31, 2013 10:43:13 AM / by Axians UK posted in IBM, cost, disaster recovery, survey, blade suppliers, hardware set up, blade, Qflex, Other, Converged Systems, idc, Integrated systems, Imtech, Infrastructure, Visibility, Juniper Networks